LDAP
Lightweight directory access protocol (LDAP) is a protocol that helps users find data about organizations, persons, and more. LDAP has two main goals: to store data in the LDAP directory and authenticate users to access the directory. It also provides the communication language that applications require to send and receive information from directory services. A directory service provides access to where information on organizations, individuals, and other data is located within a network.
The most common LDAP use case is providing a central location for accessing and managing directory services. LDAP enables organizations to store, manage, and secure information about the organization, its users, and assets–like usernames and passwords. This helps simplify storage access by providing a hierarchical structure of information, and it can be critical for corporations as they grow and acquire more user data and assets.
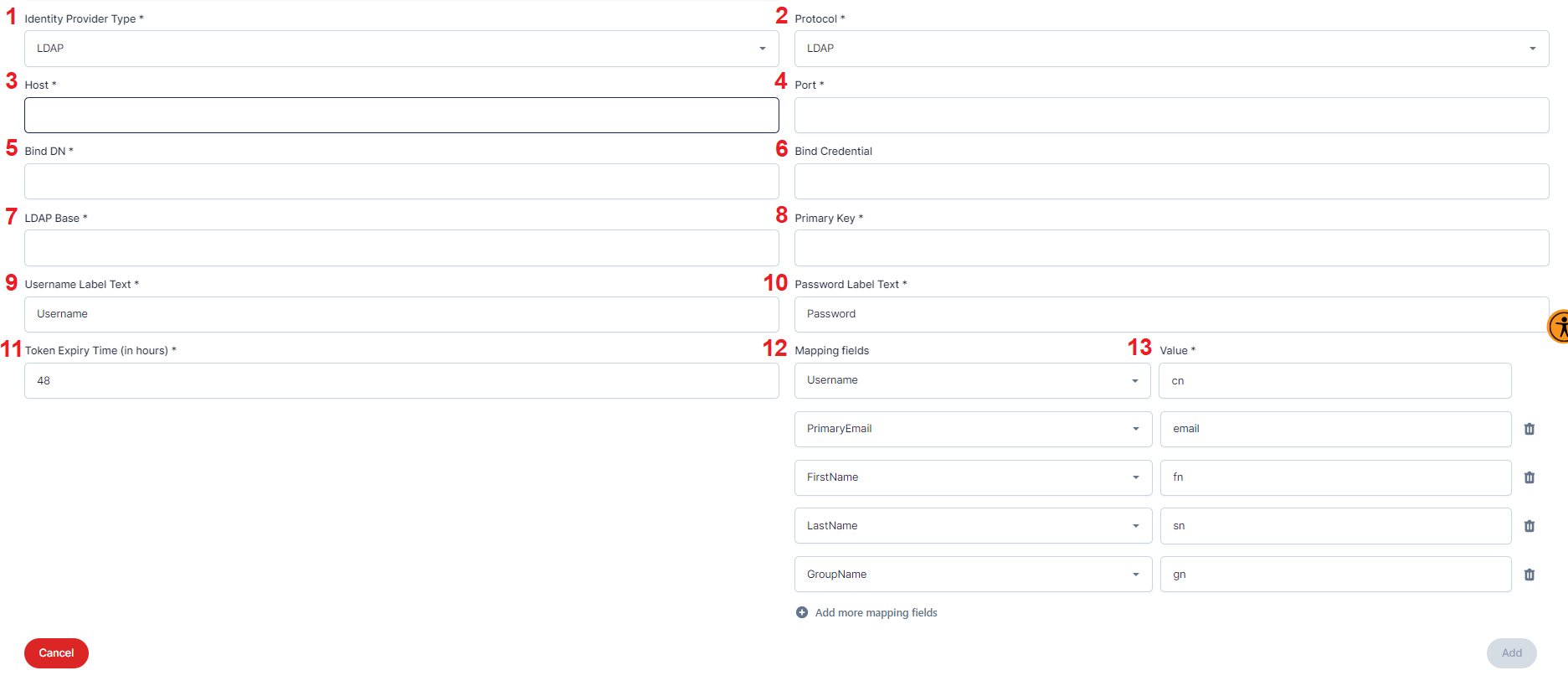
Identity Provider Type
Refers to the category or specification of an identity provider used for authentication and authorization services, often in the context of single sign-on (SSO) and user access management. From this dropdown, select the LDAP Identity Provider.
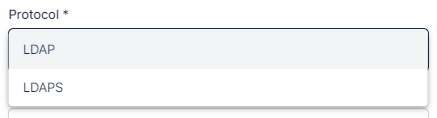
Protocol
Is a set of rules and conventions that govern communication and interaction between devices, systems, or entities to enable data exchange and interoperability. From this dropdown, select the protocol for LDAP Identity Provider.
Host
Refers to a computer or server that provides services, resources, or data to other computers or devices on a network or the internet. It is a central element in network communication. Enter the hostname of the LDAP Identity Provider here.
Port
In networking is a specific endpoint through which data is exchanged between a computer or device and a network or the internet. It's like a door that allows communication and data transfer. Enter the port number of the LDAP Identity Provider here.
Bind DN
Stands for "Bind Distinguished Name" and is used in LDAP (Lightweight Directory Access Protocol) for authentication. It is a distinguished name used to authenticate and authorize access to directory information services. Enter the Bind DN/User Name for the LDAP Identity Provider.
Bind Credential
Refers to the username and password or security credentials used for authentication when accessing a system or service, often in protocols like LDAP or for secure API authentication. Enter the Bind Credential/Password for the LDAP Identity Provider here.
LDAP Base
Refers to the starting point or root location within a directory tree in LDAP (Lightweight Directory Access Protocol) where searches or directory operations begin. It specifies the context for LDAP queries and provides a reference point for finding directory entries. Enter the LDAP Base of the LDAP Identity Provider.
Primary Key
(Lightweight Directory Access Protocol), there isn't a concept of a "Primary Key" as you would find in traditional relational databases. Instead, LDAP uses Distinguished Names (DNs) as the primary means of uniquely identifying and accessing directory entries. Each LDAP entry has a DN, which is a hierarchical path that uniquely identifies that entry within the LDAP directory tree. DN serves a similar purpose to a primary key in databases, as it ensures the uniqueness and integrity of directory entries. Enter the primary key of the LDAP Identity Provider here.
Username Label Text
Refers to the descriptive text or label associated with an input field where users are expected to enter their usernames or user identifiers. It provides users with guidance on what information is expected in that field. Enter the Username Label Text of the LDAP Identity Provider here.
Password Label Text
Is the descriptive text or label associated with an input field where users are required to enter their passwords. It serves to inform users about the type of information that should be provided in the password field for authentication purposes. Enter the Password Label Text for the LDAP Identity Provider here.
Token Expiry Time(in hours)
Refers to the period during which a security token, such as an access token or session token, remains valid for authentication or authorization purposes. Enter the Token Expiry Time here in hours.
Mapping field
Is a term commonly used in data integration and transformation. It typically refers to a data field that links or associates data from one source to a corresponding field in another source. Here are multiple dropdowns. From these dropdowns, select the mapping variables.
Value
The data within a mapping field that connects or associates data from one source with its counterpart in another source, facilitating data integration and transformation. Here are multiple dropdowns. From these dropdowns, select the mapping values.
